Hackers are increasingly using domain name system (DNS) records to hide malware, a tactic that poses significant challenges for cybersecurity. As reported on 2025-07-16 15:15:00, this method allows malicious scripts to bypass traditional defenses.
- Malware hidden in DNS records
- DNS traffic often unmonitored by defenses
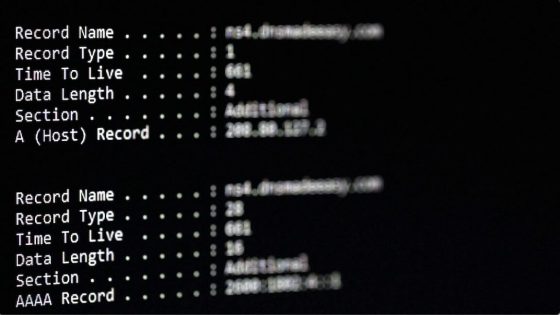
- Hexadecimal encoding used for malware storage
- TXT records store arbitrary text data
- DNS requests used for malware retrieval
- Encrypted DNS increases monitoring difficulty
This alarming trend highlights how DNS traffic is often overlooked by security tools, making it a prime target for cybercriminals. By stashing malware within DNS records, attackers can retrieve malicious binaries without raising red flags, complicating detection efforts.
This new technique raises crucial questions about the effectiveness of current cybersecurity protocols. Can organizations adapt quickly enough to counter these evolving threats? The implications are significant:
- Increased need for advanced monitoring of DNS traffic globally.
- Potential rise in cyberattacks affecting businesses and individuals.
- Urgent calls for enhanced security measures, including DNS over HTTPS and DNS over TLS.
Looking ahead, organizations must invest in innovative security solutions to stay ahead of these sophisticated tactics. Are you prepared to protect your network?










![Metroid Prime 4: Beyond "Out Now" Poster Spotted In London [Update]](https://news.faharas.net/wp-content/uploads/2025/06/Metroid-Prime-4-Poster-Spotted-in-London-–-Is-the-560x315.jpg)



















